Things move fast on the Internet. On Wednesday, Twitterank set a speed record.
Around midday, Twitterrank took hold of the twitosphere in the form of self-promoting tweets, published by the program itself as people looked up their ratings. A few hours later came the backlash, as many speculated about whether the simple ratings application was really a phishing scam. Panic ensued, especially after ZDNet’s Oliver Marks posted an article about user gullibility. Passwords were changed. The programmer responded. A parody was created. Twitter spent the latter part of the day responding to user complaints. All that dust will soon settle, and what will remain is a real issue about trust and authentication.
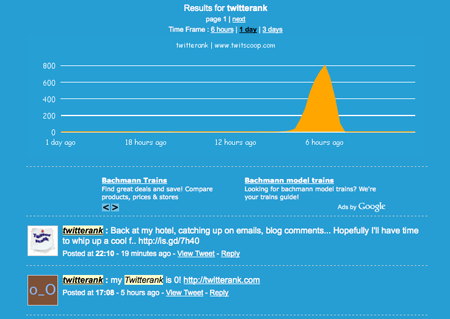
The initial surge was due to the checked-by-default option to post your ranking
By day’s end, Twitterank had gone from definite scam to poorly executed app
Louis Gray had a great post reflecting on this whirlwind. In the summary was this speculation about worst-case scenarios for a successful phishing expedition on Twitter:
The downsides of somebody hacking into my Twitter account and getting my credentials are low to begin with. In theory, if my account were compromised, they could Tweet on my behalf and make me look like a fool for some time, until I managed to get to Twitter support. In the meantime, you’d be sure to hear about it, and I assume others would be vocal in my favor. Another concern would be if you or I used the same login and password combination on other services. The perpetrator could then guess your ID on other services, or even access your financial records or anything else sensitive. But again, given the other Twitter developers’ comments in regards to OAuth, I tend to believe this is something the coders are working around, and I don’t think this is a mass account grab.
Authentication in the API is currently used for two purposes:
- To impose rate limits on a given account (something that is also handled through IP now, in the absence of authentication to some of the more open methods)
- To grant access to data that is otherwise not open to the public, namely changes to the content or settings of the account and viewing private member status updates
Wednesday’s meme lit a fire under that old debate about how big of a priority it should be for Twitter to address improved authentication to the API, but the fact remains that all of the hundreds of applications that have been built off of the API have had to deal with this issue. This isn’t something new, nor is it crippling.
Is Twishing worth the effort?
The list of things you can do with someone’s Twitter account information seems long but is in practice quite limited. Most of what you see by logging into the web site is already readily available through the API without that authentication. Many of these things are mostly harmless. A hacker with stolen authentication could mostly annoy, but assuming the darkest intents there are some holes that might be attractive.
It is important to note that several of these things can be done automatically through the Twitter API. That means that a strategy of changing your password after the fact won’t work if your account has already been compromised as part of the function of the third-party application. In the lists below, * indicates functions are only available on the Twitter web site, not the API.
Controlling
- Change your Twitter password.*
- Change the email address used for this account (which cannot be used for another accound).*
These are the most obvious things a hacker could do, denying you access to your own Twitter identity. There are failsafes, however, in the form of Twitter’s great customer service track record and historical willingness to help people reclaim their identity. They do keep backups of this data, so even if you are blocked out one day, there is nothing irreparable about it. Also, Twitter allows only one account per email, making this an unattractive target.
Invading
- View direct messages, sent and received
- View protected account timelines, if they already let the authenticating user follow them
- View the mobile phone number used by the member for updates (if configured)*
There is some information that just isn’t available without your Twitter authentication. People who protect their accounts and trust you enough to allow you to follow what they post would be vulnerable to someone coming in and capturing their tweets (which in itself should be a reason to just eliminate the “protected” account option altogether—nothing is private, really). There is also access to the phone number you use for your updates. In some cases, this will be a personal number that might not be widely distributed or even published elsewhere. Finally, the hacker could access all of the private messages you exchanged with others in your group. Many people delete them, but for some that is a place to store reminders or interact with other third-party apps with content you don’t want to get out.
Deceiving
- Send a direct message
If there is a scary bit in all of this, it probably isn’t the posting in the public timeline but rather using the existing trusting relationships and a back channel to try to convince others in your follow net to click on the links. It’s the same basic principle as using a gmail contact list to send a spoofed email from a “friend.” The connotation of a direct message is one of greater trust. In order to exchange direct messages, you have to mutually follow another member. Not everyone sees or even uses their direct messaging, so it is easier to trust it as important. A phisher could use this implicit relationship to send a nefarious link that the recipient would be inclined to click.
Stealthing
- Remove a block on another member
- Favorite a tweet.
- Remove a favorited tweet.
There are other changes a hacker could make that would be hidden from view. In mass, compromised accounts could be scanned for blocks on a spammer account and they could be removed, allowing them to then force the member to follow that account. This could be done through API interactions without ever letting the account holder know what is happening. Favoriting is not used by many people, nor does it have much value yet for third-party developers. However, a hacker could target a few preferred tweets with marketing links and make sure they appear on the user’s favorites list. These things are difficult to monitor.
Screaming
- Changing other user profile info, like description, web link and full name*
- Post a status update
- Uploading a different avatar picture*
- Mucking with the theme design, color scheme or background image of the Twitter profile web page*
- Changing location of the user
Some of the changes would be very visible, like posting status updates. Less obvious but equally as visible would be gaining access to the member’s web page to upload a new avatar or background image, or making changes to the web link or description for the member profile. Because these are so visible and involve unauthorized access to an account, there is probably a disincentive for a spammer to try to change your avatar to an advertising icon. There is some implicit accountability the person is not simply seeking disruption. You may not notice a change to your profile web link, though.
Damaging
- Delete a published tweet
- Block another member
- Delete an existing direct message
- Change your follow network by following or unfollowing people
Some of the things that are available to an authenticated user involve removal of content. Deleting a public tweet may or may not be noticed, but odds are much better that direct messages aren’t reviewed as frequently. Users could be targeted with massive blocking campaigns using stolen accounts, causing some reputation problems or damaging relationships. There really isn’t an incentive for a phisher to do this. It is the electronic equivalent of knocking down someone’s mailbox as you drive by. Presumably, Twitter could restore to an earlier state to fix the damage.
Annoying
- The ability to toggle on or off the private status of the account.*
- Change the general device used.
- Change whether direct messages are all that is sent to the device.*
- Change the sleep settings that temporarily disable device notifications during certain hours (i.e. at night while you’re sleeping)*
- Adjusting the notification settings, which include when you get email, what kinds of replies you see, and whether you want to be “nudged” after a period of activity*
If you targeted a specific user, maybe turning off device notifications or scheduling them to only show up at night would be disruptive if it cost that person sleep or made them miss a big meeting. Most of these changes, however, are merely annoyances that would damage Twitter more than the individual.
Responsible programming
Much of this maelstrom is due to the apparent lack of value that Twitterank offers. The site is somewhat ugly, by the creator’s admission hastily added. There is no context or explanation about why this ranking is a benefit. Once submitted, all you get is a cryptic number that ranges (at least) from single digits up to the 200s. Unlike Twinfluence and Twitter Grader, which attempts to offer an argument for both value and explanation of their analytics, there is nothing about Twitterank that screamed legitimacy.
I was reminded of a study former Indiana University professor Markus Jakobsson did a few years ago in Bloomington. After wrangling with the university IRB about the methodology, he had phishing emails sent to the IU community. The researchers didn’t use any of the sensitive data, but they did note who was willing to click on such links and enter valid data. Twitterank had the scent of that kind of academic work, but I think the presence of the blog renders it a poorly executed Twitter application and nothing more curious than that.
To his credit, the creator of Twitterank—a programmer at Google doing this as a side project—responded to all the criticism and histrionics with some changes, not the least of which was context (he added a scale to let you know where the number fits into the known Twitterverse) and a link to his identity. Those are the types of clues people look for when determining whether to trust a site.
Wednesday’s excitement on Twitscoop notwithstanding, I’m not discouraged from using third-party applications that ask for my account access. However, it is clear that it is an issue that Twitter should invest some resources in solving, on both technical and PR fronts.
Alex Payne and the API team have had plans on the table to work better authentication into the data access for a while. The bigger priority at the moment (and related to the success of any authentication scheme change) is to get the search and data APIs synchronized. The best strategy for the interim is for third-party programmers to assume some responsibility about the quality of what they put out in the world, understanding that the more cues one can give that your effort is legit, the better it will be for the entire Twitter community.
5 replies on “The Limited threat of Twishing”
The Limited threat of Twishing | Twitterank may not be a scam but the execution invites one | BlogSchmog
[…] } $(‘fade’).style.display=’block’; $(‘light’).style.display=’block’; } 2 Clips The Limited threat of Twishing | Twitterank may not be a scam but the execution invites one | BlogSc… Submitted by Louisgray from Delicious 52 minutes […]
Ryo Chijiiwa convinced Oliver Marks to let him use the ZDNet channel to explain himself. He tweeted as he iterated the Twitterank site that his host was threatening to shut down his server, thanks to a phishing complaint. Hopefully, the Twitterverse will settle down in the morning and let him iterate his idea more completely.
Excellent insights, Kevin. I was quite intrigued by it all last night and was curious what you thought about it. 🙂
[…] I can't get into my …http://yankee-lifeinthewoods.blogspot.com/2008/11/blogger-probs.html The Limited threat of Twishing Wednesday’s excitement on Twitscoop notwithstanding, I’m not discouraged from using third-party […]